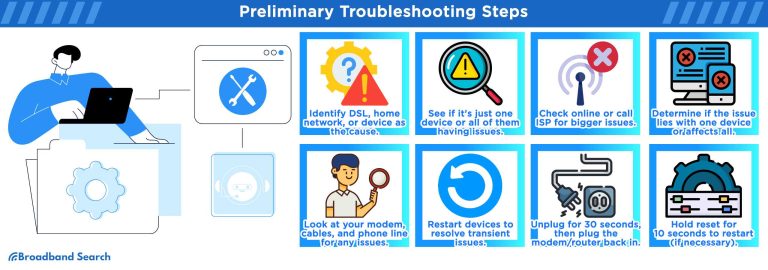
To monitor WiFi usage and activity logs effectively, you can use built-in router tools or dedicated monitoring software that tracks connected devices and their data consumption in real-time. Regularly checking these logs helps identify unusual activity, optimize network performance, and ensure security. Implementing simple monitoring methods allows you to stay aware of how your network is being used and takes quick action if needed.
Monitoring your WiFi usage involves accessing your router’s admin panel or using specialized apps that provide detailed insights into connected devices and data flow. By setting up alerts or logs, you can keep an eye on network activity, detect unauthorized access, and manage bandwidth efficiently. It’s a straightforward process that empowers you to maintain a secure and well-functioning WiFi network.
When it comes to keeping track of WiFi activity, it’s important to understand what’s happening behind the scenes. Whether you’re managing a home network or a business setup, monitoring tools give you visibility into device activity and data usage. This way, you can troubleshoot issues, prevent security breaches, and ensure fair bandwidth distribution—all with minimal effort. Let’s explore simple ways to keep tabs on your WiFi network and maintain control over your digital space.
How to Monitor WiFi Usage and Activity Logs
Understanding Why Monitoring WiFi Usage Is Important
Monitoring WiFi usage helps you see which devices are connected to your network and what activities they perform. It can reveal unauthorized users or suspicious activity that might compromise your security. By keeping an eye on your WiFi logs, you gain control over your network and can troubleshoot issues faster.
How WiFi Usage Monitoring Works
WiFi usage monitoring involves tracking data traffic on your network. Devices or tools gather information about what websites are visited, how much data is transferred, and which devices are active. This information is stored in activity logs that you can review anytime.
Choosing the Right Monitoring Method
There are several ways to monitor WiFi activity, from built-in router features to third-party software. Your choice depends on your technical skills and how detailed you want the reports to be. Consider options like router logs, network monitoring apps, or professional network management tools.
Using Router Built-in Features
Most modern routers come with basic monitoring tools. These built-in features often show connected devices, data usage, and sometimes activity history. Access your router’s admin panel through a web browser using its IP address to view these logs.
Installing Network Monitoring Software
Third-party software can offer more detailed insights. These tools can track real-time data, generate detailed reports, and send alerts about unusual activity. Popular options include GlassWire, NetBalancer, and Wireshark.
Setting Up Your Monitoring System
Setting up requires configuring your router or software correctly. Enable logging features, set thresholds for alerts, and specify what data you want to track. Proper setup ensures you get accurate and useful logs.
Enabling Router Logs
Log into your router’s interface and navigate to its logging or tracking section. Enable activity logs, specify log retention periods, and choose whether to email logs or store them locally.
Installing and Configuring Monitoring Software
Download and install your chosen software on a device connected to your network. Follow setup instructions to specify monitored devices and data types. Schedule automatic scans and reports for regular updates.
Reviewing WiFi Activity Logs
Regular log review helps catch issues early. Look for unfamiliar devices, spikes in data usage, or access to inappropriate websites. Use filters to narrow down the information and focus on suspicious activity.
Understanding Log Data
Logs typically include device information, timestamps, data transferred, and visited URLs. Familiarize yourself with log formats to interpret the data correctly. Recognizing patterns helps identify normal versus abnormal activity.
Spotting Unauthorized Devices and Activity
Compare connected device lists with known devices. Look for unfamiliar IP addresses or MAC addresses. Detect unusual data spikes or access to blocked sites as potential signs of intrusion or misuse.
Enhancing WiFi Security During Monitoring
While monitoring is vital, it’s equally important to protect your network. Use strong passwords, enable WPA3 encryption, and disable WPS. Keep your firmware updated to patch security vulnerabilities.
Setting Up Alerts and Notifications
Configure your router or software to alert you about unusual activity. Notifications can inform you of new device connections or bandwidth surges, allowing rapid response.
Managing User Access
Limit WiFi access to trusted users. Create separate guest networks for visitors and monitor their activity separately. Maintaining strict access controls reduces security risks.
Advanced Techniques for Monitoring WiFi Usage
For larger or more complex networks, consider deploying advanced tools like network analyzers or enterprise-grade management systems. These solutions offer deeper insights and centralized control.
Using Packet Capture Tools
Tools like Wireshark capture data packets to analyze detailed network traffic. This method helps identify malicious activity, malware, or data leaks at the granular level.
Implementing Network Segmentation
Segmenting your network divides it into smaller, manageable parts. It helps contain security issues, streamline monitoring, and improve overall network performance.
Legal and Privacy Considerations
Monitoring network activity must respect user privacy and legal guidelines. Inform all users if their activity is monitored, and avoid tracking personal data without consent. Always adhere to local laws.
Troubleshooting Common WiFi Monitoring Issues
Sometimes logs may show missing data or false alerts. Ensure your monitoring tools are correctly configured and updated. Restart devices or software if necessary, and verify network connections.
Dealing with Limited Router Capabilities
If your router lacks advanced features, consider upgrading to a model with better management tools. Alternatively, supplement with third-party software to enhance monitoring.
Addressing False Positives
Sometimes, normal activity triggers alerts. Fine-tune your thresholds, and review logs carefully before taking any action to avoid unnecessary disruptions.
Maintaining Your WiFi Monitoring System
Regularly update your monitoring tools, review logs, and adjust settings as needed. Consistent checks help maintain accurate data and secure your network effectively.
Updating Firmware and Software
Firmware updates often patch security holes and improve features. Keep your router and monitoring applications up to date to ensure compatibility and security.
Periodic Log Review and Analysis
Schedule weekly or monthly reviews of your logs. Look for trends, unusual activity spikes, or new devices that could indicate security issues.
Related Topics to Explore
Other helpful areas include understanding WiFi encryption protocols, setting up parental controls, or optimizing your WiFi network for better performance. These topics complement your monitoring efforts and help create a safer, more efficient network.
By carefully selecting your monitoring tools, reviewing logs regularly, and maintaining your network’s security, you can keep your WiFi environment safe and efficient. Effective monitoring not only helps you spot issues early but also provides peace of mind knowing your network is protected against threats.
How to Check Browsing History on a WiFi Router
Frequently Asked Questions
What tools are effective for tracking WiFi activity on your network?
Effective tools for monitoring WiFi activity include network monitoring software such as Wireshark, Paessler PRTG, and GlassWire. These tools provide real-time insights into connected devices, bandwidth usage, and data traffic patterns. Most of these applications allow you to set alerts for unusual activity, helping you identify unauthorized or excessive usage quickly.
How can I check which devices are connected to my WiFi network?
You can view connected devices through your router’s admin interface. Log into your router’s web portal, usually by entering its IP address into a browser. Once logged in, navigate to the section labeled ‘Connected Devices,’ ‘Device List,’ or similar. This list displays all devices currently accessing your network along with their IP addresses and MAC addresses, enabling you to monitor and manage device access effectively.
What steps should I take to review WiFi activity logs over a specific period?
Access your router’s logs via the admin dashboard, where activity records are stored. Depending on your router, logs can often be exported or viewed directly. For more detailed analysis, consider using third-party network monitoring tools that track activity over selected time frames. Regularly reviewing these logs helps spot unusual patterns, such as large data transfers or unauthorized device connections.
How do I set up alerts for unusual WiFi activity?
Most modern routers and monitoring tools offer alert features. To set this up, access the settings menu and locate the alert or notification options. Configure alerts based on specific triggers like high bandwidth consumption, new device connections, or repeated failed login attempts. Enabling these notifications helps you respond quickly to potential security issues or misuse of your network.
Are there any privacy concerns when monitoring WiFi activity logs?
Monitoring WiFi activity logs primarily involves tracking network usage and connected devices, which is generally within your rights as the network owner. However, avoid inspecting the content of data packets unless necessary, as this can raise privacy concerns. Always ensure your monitoring practices comply with local laws and inform users if appropriate, especially in shared or public networks.
Final Thoughts
To monitor WiFi usage and activity logs effectively, start by accessing your router’s admin panel. Many routers offer built-in tools to view connected devices and track internet activity. Use network monitoring software for detailed insights and real-time alerts. Regularly checking these logs helps identify unusual activity and maintain network security effortlessly.
I’m passionate about hardware, especially laptops, monitors, and home office gear. I share reviews and practical advice to help readers choose the right devices and get the best performance.